Nist System Security Plan Example
Nist system security plan example. More information about System Security Plans can. The system security plan delineates responsibilities and expected behavior of all individuals who access the system. The Special Publication 800series reports on ITLs research - guidelines and outreach efforts in information system security and its collaborative activities with industry government and academic organizations.
Thorough recovery strategies ensure that the system may be recovered quickly and effectively following a disruption. O Information system security plan and documentation o Security concerns in system management o Technology acquisition o System access use and resource security o System and data integrity. Insider threats are security breaches or losses caused by humans -- for example employees contractors or customers.
Despite the acknowledged importance of enterprise risk management NIST explicitly limits the intended use of Special Publication 800-39 to the management of information security-related risk derived from or associated with the operation and use of information systems or the environments in which those systems operate 5System owners and agency risk managers should not use this narrow. Security on February 11 2019 the President issued an Executive Order EO 13859 directing Federal agen-. The following Incident Response Plan is intended to provide an example of how a policy and plan can be written.
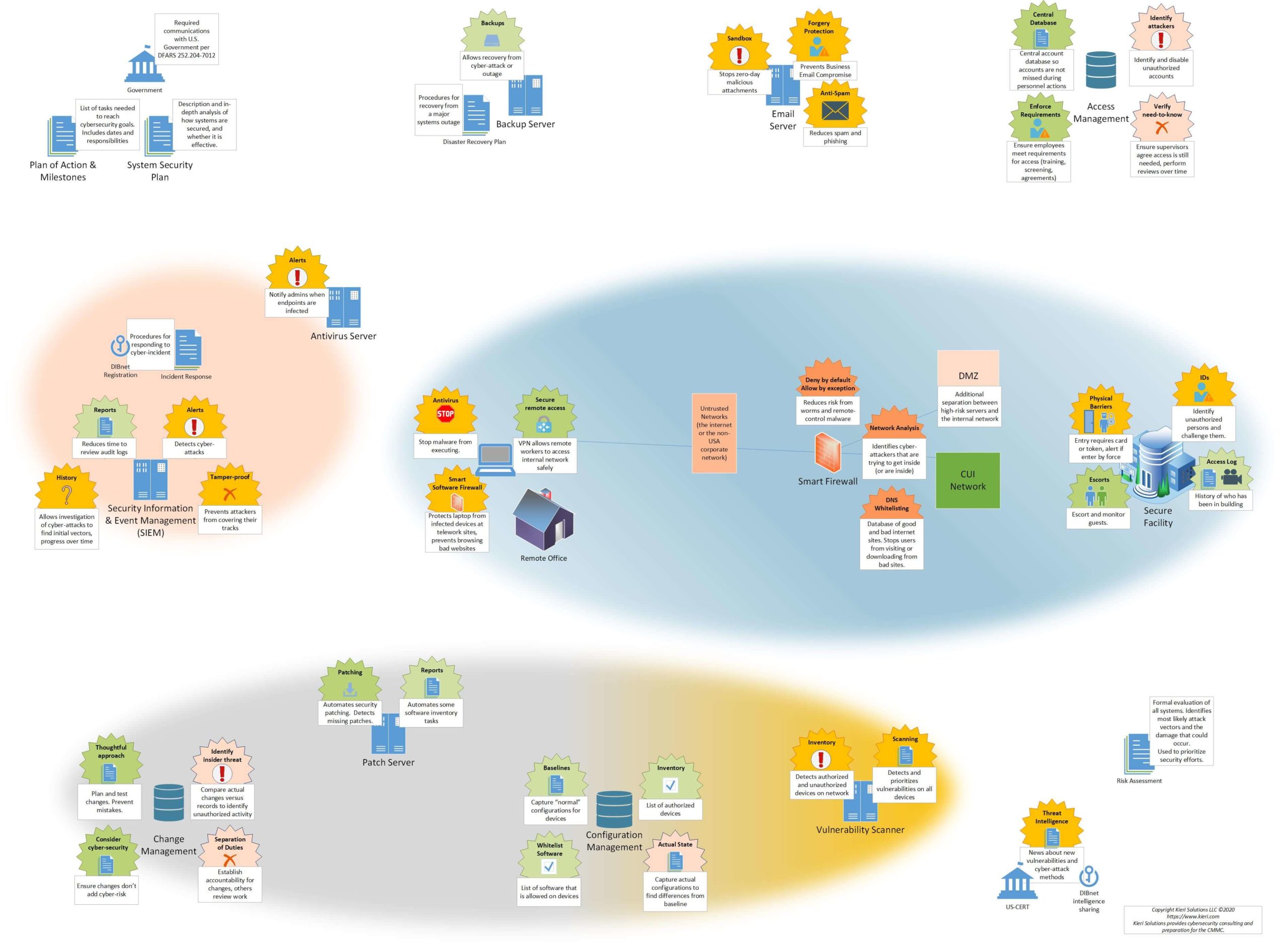
This System Security Plan provides an overview of the security requirements for the Information System Name Enter Information System Abbreviation and describes the controls in place or planned for implementation to provide a level of security appropriate for the information to be transmitted processed or stored by the system. IT IS PROHIBITED TO DISCLOSE THIS DOCUMENT TO THIRD -PARTIES Page 3 of 133 WITHOUT AN EXECUTED NON-DISCLOSURE AGREEMENT NDA INSTRUCTION ON FILLING OUT THE SSP TEMPLATE. Technology NIST A non-regulatory federal agency within the US.
The plan also ensures the successful recovery of the affected system. Have a plan for saving data running the business and. NIST to issue a plan for Federal engagement in the development of technical standards and related tools in support of reliable robust and trustworthy systems that use AI technologies.
Technical and physical standards and guidelines for the cost-effective security and privacy of other than national security-related information in Federal information systems. This requires a careful risk assessment and analysis of the impact of incidents on different data and information. Federal guidance clearly places the responsibility for system security plan development with the information system owner defined in Special Publication 800-37 as an organizational official responsible for the procurement development integration modification operation maintenance and disposal of an information system emphasis.
Each agency must evaluate their unique circumstances and incorporate those into their plan. The absence of a system security plan would result in a finding that an assessment could not be completed due to incomplete information and noncompliance with DFARS clause 252204-7012 NIST SP 800-171 DoD Self Assessment Methodology.
NIST 800-53 offers a catalog of security and privacy controls and guidance for selection.
It is not intended to cover all possible situations. Thorough recovery strategies ensure that the system may be recovered quickly and effectively following a disruption. For example data access and quality. The recommendations below are provided as optional guidance forincident response requirements. The Special Publication 800series reports on ITLs research - guidelines and outreach efforts in information system security and its collaborative activities with industry government and academic organizations. Technology NIST A non-regulatory federal agency within the US. For example if the attack resulted from an unwitting employee opening an Excel file as an email attachment implement a company-wide policy and training on how to recognize and respond to a phishing email. The NIST Risk Management Framework RMF provides a comprehensive flexible repeatable and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems and links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal. Each organization should choose controls based on the protection requirements of its various content types.
Insider threats are security breaches or losses caused by humans -- for example employees contractors or customers. The system security plan delineates responsibilities and expected behavior of all individuals who access the system. The purpose of this security plan is to provide an overview of the security of the System Name and describe the controls and critical elements in place or planned for based on NIST Special Publication SP 800-53 Rev. The NIST Risk Management Framework RMF provides a comprehensive flexible repeatable and measurable 7-step process that any organization can use to manage information security and privacy risk for organizations and systems and links to a suite of NIST standards and guidelines to support implementation of risk management programs to meet the requirements of the Federal. The cost-effective security and privacy of other than national security-related information in Federal information systems. Normally we celebrate by sharing metric education resources but this year I want to use the occasion to dispel some common misconceptions about the US. The Certified Information Systems Auditor Review Manual 2006 produced by ISACA an international professional association focused on IT Governance provides the following definition of risk management.






























Post a Comment for "Nist System Security Plan Example"